Discovering Stored XSS in Wordpress Plugin YOP Polls v6.2.7 - CVE-2021-24454
Good afternoon security fanatics. Back again today with a brief walk-through of a stored XSS (Cross Site Scripting) that I recently discovered in another wordpress poll plugin. YOP Polls, active on over 20,000 sites, allows users to create interactive and aesthetic polls that are fully customizable and perfect for data collection.

Identifying Reflection
I noticed that there was options when creating a poll to allow "Other" answers. There was also an option to display these other answers on the results screen, which is likely something that a user would enable, in my opinion.
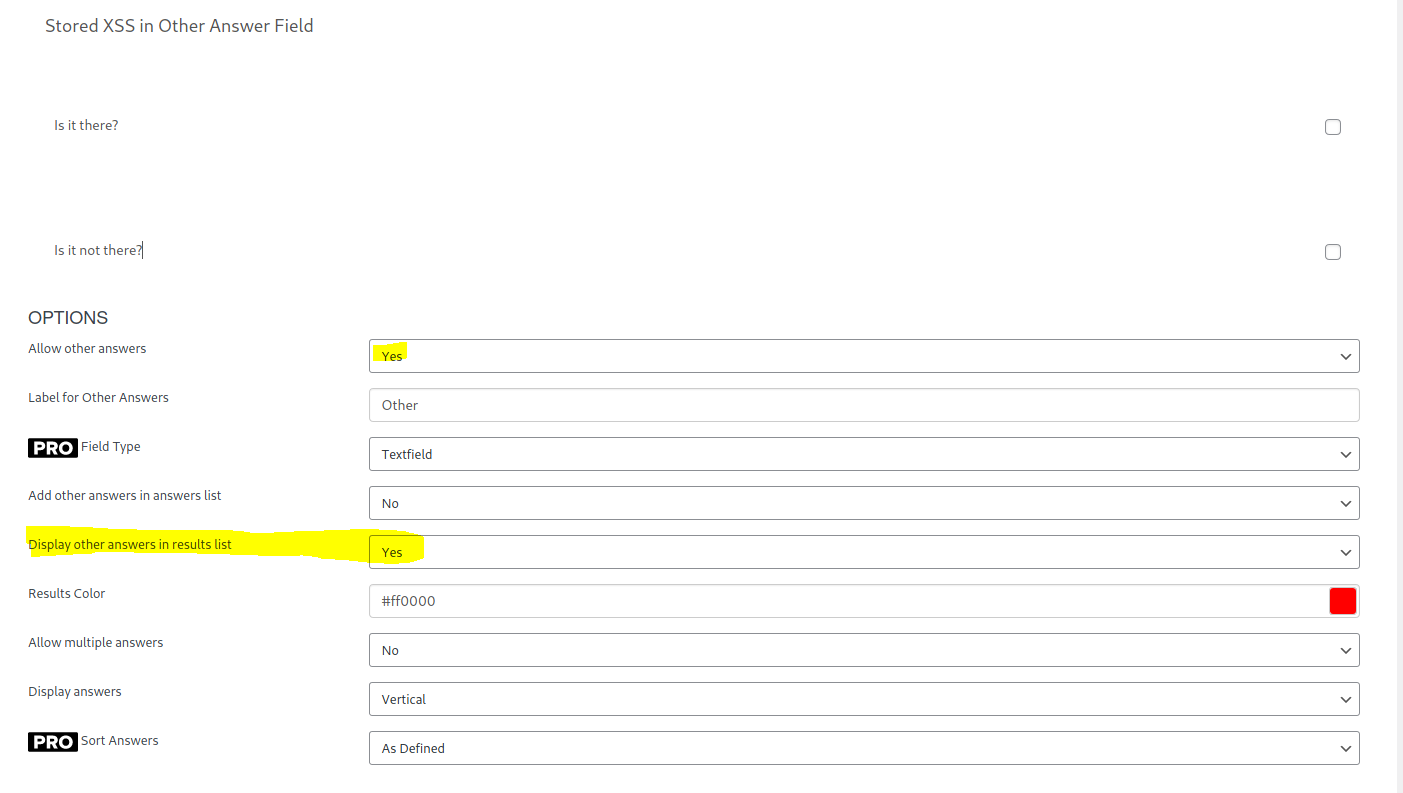
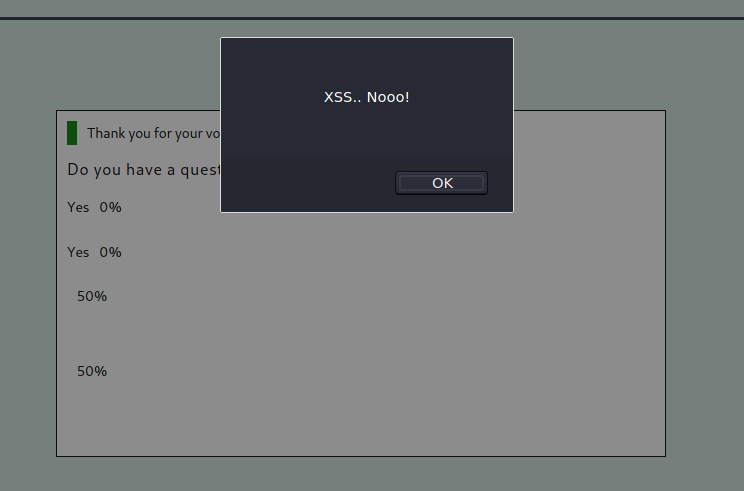
I started to play about, testing for different injection types and XSS payloads. To my surprise, the results page reflected the answer back to me as a heading when I stuck it in <h1>tags</h1>. I then opened a new browser without a session and voted to view the results page again. The heading was still there! Therefore, I concluded that I'd discovered some form of stored XSS. I checked if I could use <script> tags too, and sure enough, it worked.
Reporting the Vulnerability
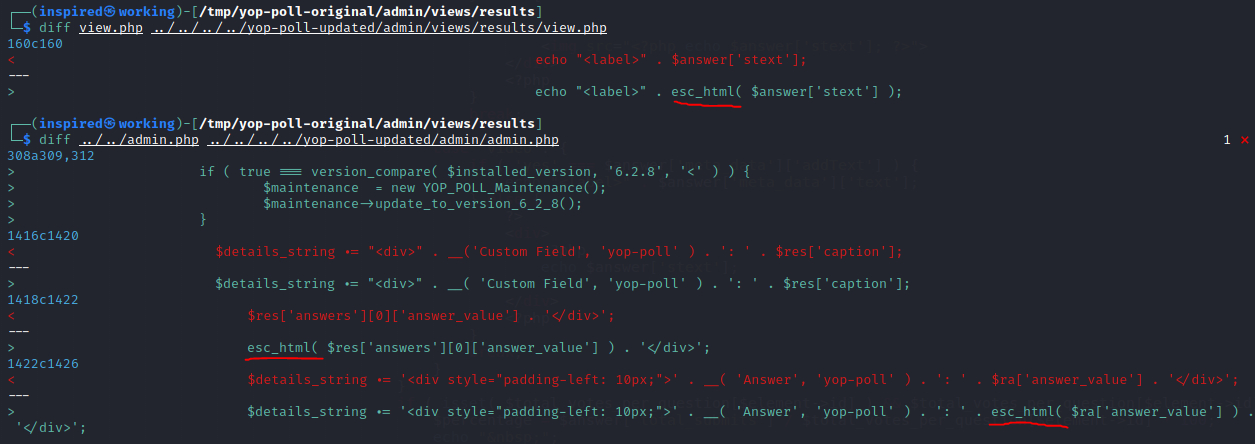
I promptly contacted YOP Polls developer and it was fixed within a week with some fantastic contact. The changes made included making use of the esc_html tags before echoing anything back to the user, as seen below.
Proof of Concept
Systems Affected
WordPress websites running "YOP Polls" plugin version 6.2.7 (older versions may also be affected).
Remediation
The update has been fixed in version 6.2.8, so it is advised to update to this version if using the plugin.
DISCLOSURE TIMELINE
June 9, 2021 1: Vulnerability identified.
June 9, 2021 2: Informed developer of the vulnerability.
June 10, 2021 1: Vendor requested proof of concept.
June 10, 2021 2: Sent proof of concept and accompanying details.
June 14, 2021 1: Vendor emails to state the vulnerability has been fixed.
June 16, 2021 1: Confirmed fix, vendor happy to disclose the vulnerability.
June 17, 2021 1: Requested CVE Number.

