OSEP Review 2021 - Offensive Security Experienced Pentester

What's up, security folks! Today I'll be putting pen to the paper and going over my thoughts on the Evasion Techniques and Breaching Defenses course from Offensive Security, colloquially known as the OSEP. I passed my exam at the end of November, so consider this a review of the updated exam (Post leak)! I'll go over the contents of the course, how I prepared for the exam and any useful tidbits that helped me along the way.
As a bit of background for those who don't know, I'm a Masters student from the UK studying Cyber Security. I don't currently have a job in the industry and do these certifications both as a way of learning and also challenging myself. They're LOTS of fun and it's extremely satisfying to pass. That being said, if anyone's reading and looking for a junior internal tester/red teamer... Get in touch ;-) Enjoy!
Course Content
Offensive Security describe this course as the next step for those who have completed their OSCP. I achieved my OSCP about a year ago, then focused on my undergraduate, and in July I decided it was time to dive back into practising my pen-testing. In terms of Active Directory experience, I took the CRTP from Pentester Academy and got most-way through HTB Offshore, but that's about it. The course syllabus can be seen below, directly from the Offensive Security website.

Overall, I believe the content of the course is great. The amount I learnt in such a short period was quite astounding. The topics are taught really well, though at first it felt quite overwhelming due to the sheer volume of low level programming concepts. As someone who had little to no programming experience in C/C++/C#, I'd advise having a baseline grip with C# at the very least to help you at the start. Each topic dives deep into the subject, exploring the reasoning behind why specific things work as they do and how they are exploitable. I've seen posts saying the methods taught are outdated for current industry standards, however, I cannot comment on this as I don't currently work in industry. All I know is that half the programs I've created that contain malicious meterpreter shellcode can now safely be transferred to my host without my AV // Windows Defender batting an eyelid, so I'm doing something right!
Keeping a log of all programs you write, the code, the instructions for use, will be invaluable when it comes to tackling the challenge labs and the exam. The course demonstrates a way to set up a Samba share on your Kali Linux device to allow access to your completed codes from every development box you're working from. Ahh yes, the development boxes. Each section comes with its own, personal instance. For example, if you're working on the Process Injection and Migration section, you'll have a development box available to connect to via RDP which has all necessary tools and Visual Studio to get started programming the tools instantly. This was a stand-out feature of the course for me, everything I needed at any point was already there, spawned on my personal instance. It made it so much easier to work, rather than fiddling with a personal development VM, transferring over necessary tools etc. Kudos!
My favourite modules of the course were related to developing AV bypasses and creating custom versions of well-known tools to avoid signature based detection. You'll work heavily with Win32APIs, explore client-side attacks via the standard Microsoft Office methods but also more advanced HTML smuggling techniques, and develop ways to destroy AMSI and execute your malicious code in memory using Powershell. The content focuses on avoiding detection by endpoint security solutions but does not cater for a Red Team/Blue Team scenario, which is why Offensive Security do not label it a course specifically for Red Teaming.
Conversely, I felt the Kiosk breakouts and enumeration was an interesting thing to include but didn't feel overly in depth or necessary, rather a bit of filler content. I enjoyed it, don't get me wrong, however I fail to see how it flows with the rest of the course. Furthermore, if you're not already up to date with basic Active Directory attacks, you better start there. The course, whilst briefly going over Active Directory exploitation for the last chapter, does not focus that heavily on how to exploit it. The course touches on ACL misconfiguration, Delegation abuse and abusing Extra SIDs to move over trust boundaries, but does not cover basic attacks such as Kerberoasting and what golden/silver tickets are. I assume this is because you're taking a 300- level course, you're really expected to know these sorts of attacks prior to taking it. I like this approach, personally, but can see why it would irritate people. However, there has to be some cut off where they assume you have pre-requisite knowledge. They do state this on the course page, to some extent.

Hence, I would highly recommend the CRTP if you've no experience in Active Directory. It definitely helped me, it's cost effective and Nikhil is an incredible tutor.
The detailed syllabus for the OSEP is available here, and is linked from the official OSEP page, if you want to know more about what you'll be learning.
Love, Love, LOVE!
So what did I love about the course, aside from the aforementioned specific chapters and incredibly well-structured lab instances?
For me, it not only taught me how to evade defences and breach internal networks, it taught me a different way of thinking. It encourages extreme problem solving, forward thinking and provisional attack chain planning. Each piece of your attack chain needed to be in place before execution, which allowed me to formulate mental systemic checklists, and I find myself using this "mindset" for every cyber vulnerability I exploit now.
The content itself is so, so in-depth. They don't just give code and tell you to compile it, they go through each code segment and explain what it's there for, and why, before helping you put it all together. There is just so, so much alpha in there. Jam-packed with incredible content, concepts and theories as well as the core fundamentals which you need to know before performing certain attacks and bypasses. The sections on Applocker and Constrained Language mode were absolutely fantastic. The videos are perfectly matched to the course, near enough, and I think watching them when I was confused about what the textual instructions were saying was invaluable. The pace is just about right for someone who has passed OSCP but hasn't been programming very much, and after a week or two of compiling, recompiling, programming, forgetting semi colons, I started to feel really comfortable in Visual Studio and working with C#. Furthermore, taking on environments such as HTB Offshore, I've successfully used the tradecraft that I learnt in the OSEP to high degrees of success, whether it's bypassing AMSI or getting a custom-built PrintSpoofer executable onto the target without detection, the stuff taught is really useful elsewhere too!
At the end of the PDF, you come to the "Challenge Labs" section. This relates to the 6 challenge labs which are in place for you to practice the skills and techniques taught against targets, and the difficulty increments throughout the targets. Labs 1-3 are "simple", in terms of a small environment, usually exploiting 1-2 things you've learnt specifically. Labs 4-6 then start to grow in size, with lab 6 being akin to the exam according to the OSEP exam guide. The labs themselves are well put together and definitely link to the course content, allowing users to demonstrate clear knowledge and put into practice their techniques against a black box target. They were thoroughly enjoyable and took a reasonable amount of time to work through. At first, I felt a bit overwhelmed but like anything, the more you do, the more comfortable you feel. I think they present the perfect level of difficulty given what I had learnt on the course, and they did a really good job of transitioning from "teaching" to "testing you" seamlessly.
Finally, I wanna give a big shout out to the student admins in the discord. Always happy to guide you with a certain problem or challenge lab without spoiling it, they encourage critical thinking and troubleshooting whilst still making you aware that the answer needs to come from your own head. Can't praise them enough, and the discord in general was a great place to ask for help with anything I didn't fully understand.
Issues? ISSUES?!
So it would be hard to have no issues with a course that spans over 3 months. Inevitably, things go wrong, break, end up misconfigured... You get what I mean. I'm going to give my honest opinion about the troubles I faced in this section and how I feel looking back at them.
I started the course in July, purchasing an OSEP and OSWE voucher as a bundle. At the time, I was on the "old" Offensive Security training library, I had a personal VPN that I connected to with a password that allowed me access to my personal labs page, my exam scheduler, challenge labs progress etc. I had originally purchased 60 days, but after taking nearly the full 60 days to just get through the PDF and fully understand each bit, I needed to extend. This is where the issues began. Offensive Security are currently in the process of transforming their courses to all work with the "Training Library". It's part of the same format that Proving Grounds is now hosted in. You have access to the course, the course videos, course content, labs, challenge labs, all in one place. You sign in with your Offensive Security credentials, and don't have to be connected to a VPN. In the middle of September I spoke to the salesman whom I bought the bundle off and explained I needed an extra 30 days. I had given 14 days notice before my labs ended, sent the money, and then awaiting the extension. Over 3 weeks later, I still had no access to the labs, because my account was being "migrated" to the new training library/system, which really messed with my timeline. Finally, and to their credit, the a Student Success Concierge personally contacted me and took the matter away and fixed it within a day or two. But that big gap for "account migration" really set me back, not being able to study or access lab materials.
After regaining access, I was working through the challenge labs, and since the new training library now has .ovpn files that are not password protected and seem to dynamically assign IP addresses, everytime I connected to the VPN I had a different IP. Why does this matter? Well, when you're compiling code with shellcode made for 1.1.1.10, then you come back to finish the challenge and your IP is 1.1.1.11, it means you have to recompile all the tools or programs you'd made for that challenge. This was absolutely infuriating, however, they did acknowledge this as an issue and for the last 2 weeks of my lab time I had the same static IP, so something has been done to fix this going forward.
Finally, the exam leak. I know this isn't Offsec's fault at all, and thanks to the incredibly smart fella who leaked them (You didn't hurt anyone as much as you hurt your fellow students). I had originally scheduled my exam for the 22nd October, my lab time ended the same day so it was perfectly lined up. A few days before, I receive the e-mail that the integrity of the exam has been compromised and all exams will have to be re-scheduled. So I was left with my lab time ending, no exam taken, and no idea when I'd be able to take the exam. After weeks of back and forward, Offensive Security provided free lab access up until my re-take was ready (25th November). However, the process of trying to get this "free" lab time was terrible. So many e-mails, one thing being said in the Discord and another thing over e-mail to support, being told I was getting a week of free labs rather than up to my exam.. It was a mess. There was a severe lack of communication with students and lots of frustration and anger. If I could change one thing, it would be the quality of communication around the situation.
Anyway, moan over, it was in no way their fault, but it was also not our fault, as students we're equally as impacted mentally and physically in terms of time, work, commitments, and this felt like it got lost.
The good news is that if you're planning on taking the OSEP in the near future, I can nearly guarantee that all the above problems have either drastically improved or are no longer an issue. It seems the migration to the new training environment coupled with the leak was an unprecedented series of events, but one which they are now starting to (thankfully) get on top of.
The Exam
It's why you're here, the holy trinity of any course review, the exam section!
Whilst I cannot delve into exam specifics for obvious reasons, I will give an overview of how I prepared and how I thought the exam compared to the course. The qualification requires you to undertake a 48-hour exam that is proctored, that is to say that you must turn your webcam on and share any screens that you are using with the proctor. They will watch you all the while you work, with the exception of pausing your webcam if you are taking a long break. However, it is still recommended to leave your screen on, if not, you must pause your VPN so you cannot continue working. Similar to OSCP, I quickly forgot about the proctor but also had issues with Chome and the screen sharing application, so ended up using Firefox. The setup was nice and quick, though seems stricter than before, I had to move any other digital devices well away from my desk so it was just my and my PC. That's a side note that if you have any notes on a tablet/digital device, ensure you transfer them to the device you're working on, as you cannot uses any device that is not proctored whilst sat working on the exam.
According to the exam guide, the exam lab "... consists of one large network with multiple machines that must be compromised. As the exam network simulates a corporate network, you will have to first obtain a foothold and then perform additional internal attacks. There are multiple attack paths through the network that will result in the same level of compromise."
I decided to do the final challenge (6) the day before and time myself, as this is supposed to be the most like the exam environment. I worked from about 11am - 11pm that day, completing the lab in 12 hours. I slept until 9am, went for a run and came back to my PC at 11:30am ready to start my exam at 12pm. I didn't elect to do any revision the morning before, and going out to clear my head was definitely beneficial. Once in the exam, I got straight into it and worked for about 18 hours straight until 6am the next day, then slept for 3 hours and came back to it. On reflection, I would've done far better with more sleep and I felt terrible but my brain was too buzzed full of ideas to lay in bed again. The goal in the exam is to either gain 100 points, or access the secret.txt file which is on the final machine in the environment.
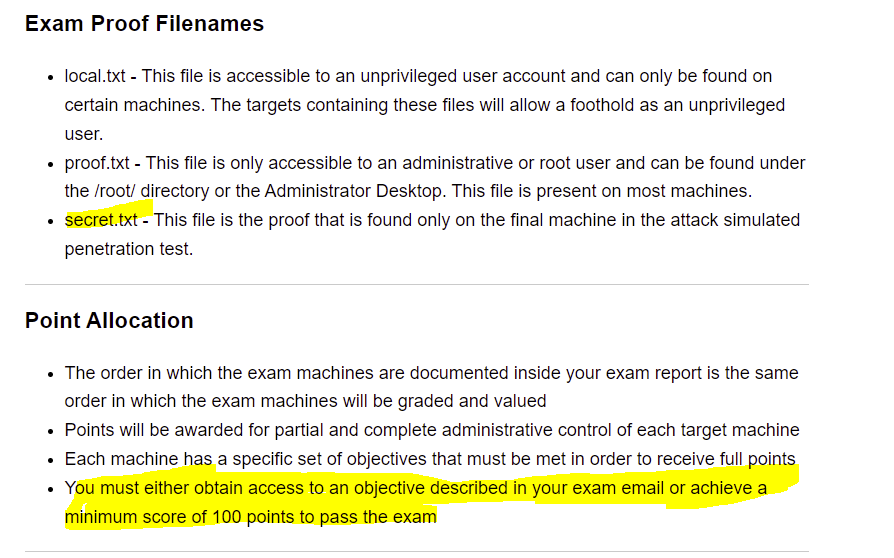
I managed to get to the secret.txt file about 4 hours after waking up, so roughly 25 hours after the exam started. I then had the remaining time to ensure my process was fully documented and attempt alternative paths, which was good fun when the pressure was off!
There has been LOTS of talk in the discord and on Twitter about the difficulty of the exam and whether or not it is buggy as they rushed to replace it after the leak. All I can say is that everything worked as intended for me, and that if something wasn't working as intended, I had to evaluate whether I was actually just going about it the wrong way or not understanding the attack vector fully. If I had to describe the difficulty, I'd say it was like the OSCP but on 'roids. Incredibly tough, very inventive and to be honest, I'd even say a bit of a masterpiece. Whoever built that, kudos, it's extremely well put together. All the reviews prior to the new exam being released seem to describe a "straight forward" exam that if you complete the PDF and challenges you will be fine. I semi-agree, but definitely feel like doing the CRTP and HTB Offshore would not be a "bad" idea in preparation for your exam, or as an alternative if you cannot crack the new exam. Furthermore, checking out harmj0y's blog is never a bad thing to read up on a huge variety of AD attacks and research that he pulls. This background knowledge is always useful to have!
Closing Thoughts
Overall, I honestly loved the course and the content. I lost some faith after the issues, but they were actually restored after the fantastic exam experience which honestly just had me grinning with how smart they made it. I recommend this course to anyone who has their OSCP and is looking to take their internal penetration testing knowledge and ability to the next level, whilst also understanding more of the underlying systems in use and how to evade endpoint detection.
Next up for me? Who knows. I have tons of University work to catch up on, I want to write more blog posts on specific AD attacks, take my OSWE, PNPT from The Cyber Mentor, finally learn some C.. Lots to do, but I'll be sure to keep this updated from time to time with anything that's worthy of a post!
Thanks for reading, and best of luck.

