ZeroPointSecurity Certified Red Team Operator (CRTO) Course - A Comprehensive Review
A review of ZeroPointSecurity's Certified Red Team Operator course.

Well hello again! It's not been all too long since my last post, but immediately after obtaining the PNPT I was hungry for the next challenge, and the Certified Red Team Operator (CRTO) from ZeroPointSecurity had long been on my radar. The course is the brainchild of Rastamouse, and he solely writes the content, maintains the course and provides support, amongst his other work. It's a pretty impressive feat in my humble opinion, to provide such a comprehensive course as, essentially, a one man army. This aside, the course has a unique feel to it. It's designed as an introduction to Red Teaming, and it now comes with an accompanying Cobalt Strike instance to get some hands on experience with one of the most used C2 commercial frameworks. It's not just about technicalities, either. There's a subtle flow from pre-engagement practices through the active engagement and it rounds everything off with post-engagement summaries and reporting information. As someone with no real-world experience in the heart of a Red Team, these little additions are eye-opening and provide a unique insight to the less glamourous side of the job. Alas, enough overview. Let's jump into the review.
Course Structure
As previously mentioned, you get to use Cobalt Strike throughout this course without having to purchase a license. This is made possible via the browser based access that the course provides, with everything being done in Snap Labs using Guacamole. This means you cannot transfer tools, unless you're copy and pasting them chunk by chunk, however you are provided with a Tools folder that contains everything you need. Further, your instances are private. There is no one else in your labs, and unless you revert them, they will continue to house your changes in between restarts. Consider it your own personal Red Team playground, and you can continue to use it after you've taken the course, too. Each section is broken down into bitesize, digestible chunks, often with a few minutes of reading on a topic, followed by some command examples and OPSEC considerations. Personally, I would read a section first, then go start up my labs and follow along with it. Some sections have accompanying videos, which do differ occasionally from the text based instructions, so definitely watch both!
The course is not designed as a challenge lab. Those of you have done the CRTP from Pentester Academy will know what I mean. It's essentially a walkthrough of of how to perform various operations using Cobalt Strike, so you won't be hunting for flags in the lab environment akin to OSCP labs, for example. There are 25 sections in the curriculum, too, so it's got a wide range of content to absorb, and it includes topics such as pre-engagement, initial attack vectors, privilege escalation and host persistence. One of the great aspects is the addition of open source blue-team software running in the environment, which you're encouraged to use to go and see what logs your attacks have left behind. Neat!
What I especially liked about the structure was the way it has been worded, succinct and to the point (Unlike my blog posts haha). Some parts were lacking in the "why", but again, this is an entry level Red Team course, not an Active Directory course, or Windows Architecture course. It teaches you how to operate a C2 framework and attempt to stay under the radar, rather than dive into the technicalities. This leads to you being pumped to get into the next section, as each part is so easy to digest. If you've done anything from Offensive Security, by god, their PDF can be a struggle to get through due to how in-depth it goes. So this is a refreshing change, but it's something to be aware of. If you're interested in the full course curriculum, you can check it out on the course page.
Pricing
The course has recently undergone a change in pricing, I believe, and now offers payment plans. I used about 40 hours in the labs, but there was no bundle option when I signed up so bought them in bundles of 10 hours. Oh yes, I forgot to mention. The course and exam are purchasable separately to the lab time, and for me, lab time was £1.50 per hour. This is a small price to pay, in my opinion, as you're getting use of a fully connected AD environment, pre-built with all the tools needed, and the use of Cobalt Strike. However, it is something to be aware of if you do not purchase the course with the 40-hour lab bundle. It is obviously optional, but following along naturally will help the information and processes stick better.
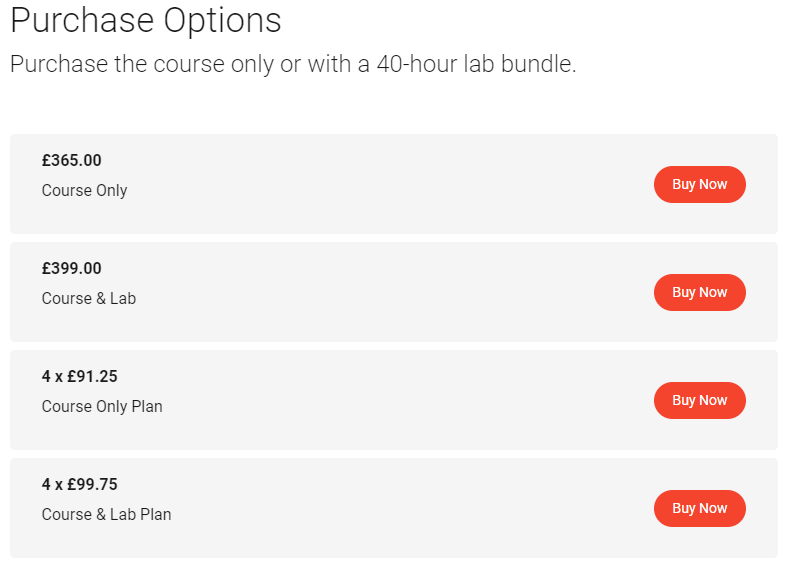
Already a pro? You can also just buy an exam attempt at £99, which is consequently the price of re-takes if you fail the one that comes with the course.
Overall, I think the course is fairly priced for the amount of information that you get and the quality of which it is presented. You're paying to share the knowledge of an exceptional teacher, learn to use (hands on) one of the most popular C2 frameworks and receiving course content updates for life. However, it should be considered that similarly to the PNPT, the drawback is that it's not something I've (currently) noticed on job requirements. But you shouldn't really be taking this with the prospect of using it to get past HR, as the majority of people taking this will likely already work in industry or have a decent-enough understanding to already be able to get their foot in the door. That's just my opinion, of course, but it seems like the natural next step for a penetration tester rather than someone fresh to the field.
Course Highlights
For this section, I'll be going over some of my personal highlights from the course and why I enjoyed that part specifically. Please bear in mind that this is subjective!
Well, Cobalt Strike Duh!
So the obvious highlight of this course is learning to use Cobalt Strike, witnessing its power, seeing how it makes tasks I previously found irritating (pivoting haha) super simple. You're taught from the very beginning: Configuring your team server, joining your operators, setting up listeners, before learning how to enumerate, attack and persist on the target network. With ease, you can execute your C# binaries in memory using the execute-assembly feature rather than dropping them to disk. It's f*cking awesome. Oh, and implement an AMSI bypass that patches the AmsiScanBuffer by just adding a line to your server setup. It's all made so simple.
Active Directory Attacks
The Kerberos section was really well explained, as I mentioned previously about the course, it's presented in a very digestible format and this part is no different. Kerberos isn't the easiest topic to understand but I think the course goes into just about the right amount of detail in terms of background, and attacks. The attacks that you go through include attacking delegation (constrained and unconstrained), DACL misconfigurations, Kerberoasting and ASREProasting, amongst others. I already knew the basic premise of these attacks, but learning to do them in-memory with Cobalt Strike is a completely different ballgame.
Defences? What Defences?
One really interesting aspect of the course was altering the default artefact's and resources that Cobalt Strike uses. The artefacts are, essentially, a template that gets patched with beacon shellcode on the fly when you, for example, generate a new EXE, or use psexec. You're taught to use a tool like Threatcheck to scan the default templates and identify what Windows Defender is identifying as malicious, and then modifications you can make to try and stop them getting flagged during signature based detection. The course teaches you the basics, and what files you need to edit, but also sets you up to go away and do your own research, potentially implementing your own methods and techniques in the constant battle with AV. However, it should be remembered that the course is a beginner course and thus, the AV isn't fully up to date, nor are the servers, but I'm positive that the underlying methodology carries over.
Credential and Token Abuse
I'd dabbled with Metasploit's migrate, naturally, and in the OSEP I'd learnt lots about the token abuse process, stealing SYSTEM tokens etc. But I felt that this course gave me a more holistic overview of how to steal tokens with Cobalt Strike and what specific technique is used, and whether this means the token will work locally or with other machines in the network. The course does a great job of breaking down these types of credential abuse attacks and where / when to use what to maximize the effect, and also to consider your OPSEC, how your actions may look to a defending team or how they may affect the current client environment.
Course Drawbacks
There are not many negatives to this course, in my opinion, but as I am in no way affiliated with ZeroPointSecurity it's only fair that I present any negatives that I experienced during the course.
Snap Labs Reliance
A small point to remember is that fact that the whole course is presented through snap labs, and whilst it was fantastic for the most part, there were sometimes connection issues which I can only assume was on their end. Guacamole would just disconnect for a little while before coming back up. It was not often at all, but obviously when it does happen, there's little that can be done aside from waiting it out.
Support
The biggest issue is naturally the support side of things, which will come as no surprise if you've been reading the whole review given that the whole of the course is created, maintained and supported by just one man. In Rasta's defence, every issue I had received a very prompt response (sub 1 hour) and a small issue in my exam was fixed for me nice and quick. He is very responsive, provided you're not asking something provided in the FAQ, but there's naturally going to be times where he is either not available (UK night time - Weekends) or busy with life in general. This presents an issue whereby if you have a problem with your exam, you could be waiting a while for any support depending on when you need it. Something to bear in mind. However, for me, there wasn't a need for much support anyway, since everything was provided in the containerised browser. If you do have an issue, you can use the contact form on the ZeroPointSecurity website (I prefer this for formal issues) or simply ask in the Discord channel for the course. Actually, if you use the search function in Discord, you'll usually find an answer to your question anyway ;-).
Anyhow, it doesn't detract from the fantastic course experience, it would just be nice to have someone available other than Rasta when you have an issue, and in terms of scaling, it's probably going to be necessary at some point.
Exam
The exam is a 48 hour, practical CTF. You are tasked to obtain 6/8 flags to pass, so 75%. The exam is, however, available for 4 days, and it's possible to pause it if you want to take a break / sleep / get some wonderful fresh air. I therefore went in with the approach of 12 hours a day spread over 4 days: One, to avoid burnout, and two, to ensure I spent some time AWAY from the screen digesting information and plotting my next step. It's an assumed breach scenario, and thus, you have access to a Kali Linux machine, Windows Attacking machine and a machine on the internal network from which you base your attack. It's done through Snap Labs again, so you're working through the browser and can't really transfer tools. That being said, everything you need for the exam SHOULD be on the machines already.
Overall, I think it's a very fair exam and everything that you need for the exam is covered, in one form or another, in the course content. You might have to alter the commands, so it's not a verbatim "Do this, do that", but if you understand the underlying attacks and enumeration required you should be fine. 48 hours, over 4 days, is a very generous amount of time and I'd expect you to run out of ideas quicker than you run out of time. That's not to say the exam is easy, I think it's on the harder end of the scale as when you're in the labs, the machines generally have no defences. This is not the case in the exam environment. You will have to really think at times, consider what defences you may be up against and analyse the best way to deal with them. If something doesn't work, consider why it's not working. What might be stopping you? I generally have a piece of paper and a pen in front of me whenever I take an exam and when I hit a roadblock, write down all the rational sanity checks that I can do to rule out certain reasons for stuff not working until I can hone in on the issue. You will have to troubleshoot, but that's going to be the same in a corporate environment too, not everything will work out of the box, but with effective enumeration and reconnaissance you should be able to identify the defences in place and bypass them effectively. Again, everything you need is IN THE COURSE.
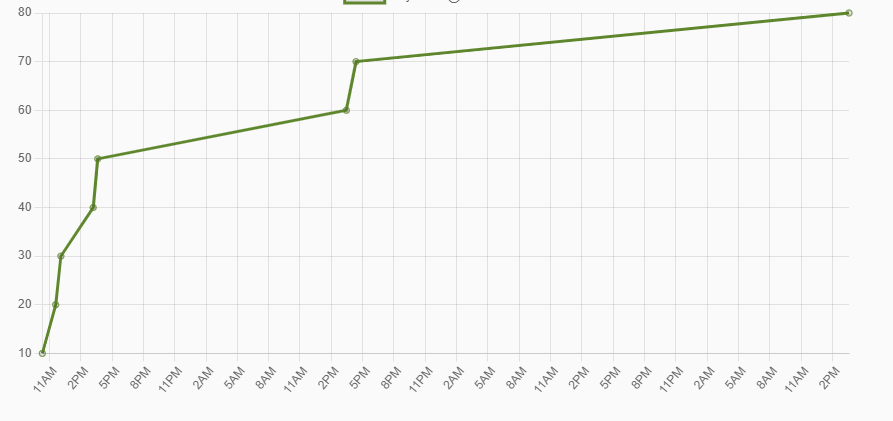
In terms of timings, flags 1-5 fell relatively quickly, as seen below. I took some time off from about 8pm, starting again about 1pm the following day after university. After obtaining the 6th flag, the 7th was nice and easy. I spent the rest of the night (until about 1am) looking for the elusive final flag, with no luck whatsoever. Then the next day I booted it up for a few hours and still couldn't work it out. I was starting to feel like I was missing something very simple, as I spent nearly as long getting the last flag as I had the previous 7!
It finally came to me right before my Sunday Roast (Yes, very British), and I breathed a huge sigh of relief as the final one fell.
It was a fun exam, compounded by the extra challenges presented that made me think harder than expected. It wasn't CTF-y in the sense that you needed to look in really abstract areas to identify a weird file or anything like that, you very much saw the path right from the start and there was no rabbit holes or cloak and daggers, which I appreciated and means you're being tested on the application of your course knowledge rather than how out-of-the-box you can think.
What's Next?
Quite right, what is next? University is starting to heat up so I'm going to get my head down and try to smash some coursework out over the next few weeks, alongside a couple of CTF's I've signed up to. I HAVE purchased a couple of Sektor7 courses, off the back of some great things I've seen in Discord chats recently, so looking forward to doing those sometime as AV evasion and custom tooling is something I'm growing ever-more interested in. I'll continue to hang out in the ZeroPointSecurity Discord, as the community there seems pretty great and it's full of people who are waaaay smarter than me!
I guess I should also start looking for a job at some point, since come October, that student safety blanket is getting whipped away ;-)
Until next time, folks.